Are you a website owner struggling with a malware infection and lost Google rankings?
You are not alone.
We recently had the pleasure of helping an insurance company restore its website and clean up its Google rankings after a successful malware removal from a website process.
In this case study, we’ll show you how we took action quickly to clean up their site and restore their hard-earned search engine rankings. Following our simple steps, your website can be back in good standing and safe from malware. Keep reading to find out how!

On December 31, 2022, Danielle Peffers saw an email notification that the website of our SEO Agency insurance clients was down.
She checked the website and saw that the site was offline.

Danielle then tried to pull the website up on Chrome and was met with a Critical Error when trying to open the website at that time.
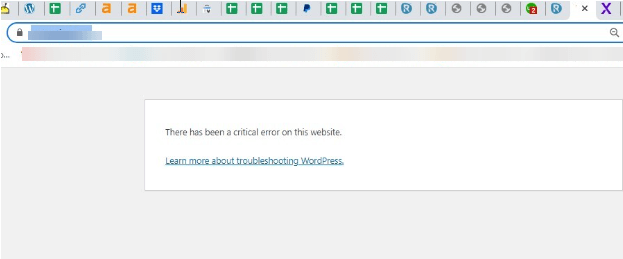
Danielle then contacted hosting to get the website live again.
The web host representative informed her it was a problem with the design and not hosting.
Danielle then reached out to our developers, that was leaving for a week-long cruise to get the site live.
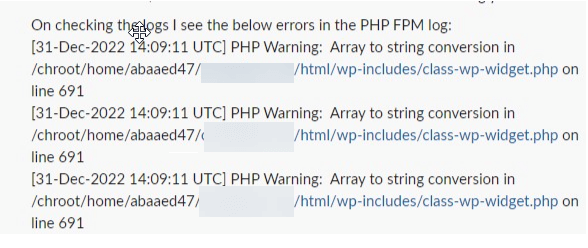
Our developers tried to get the backup site up and running but kept receiving errors.
For some reason, the backup would not load for them.
The developers then disabled all the plugins on the site to see if that would bring the site back online.
This attempt did not work either.
At this point, we knew the site DID NOT crash from plugin-related issues.
We then informed the client the site was down.
Here is the email we sent:

The client then reached out to the host for a resolution to the problem.
The host restored a backup of the site, and it went back online. Which they did not do for Danielle when she had asked for help several hours earlier.
On Tuesday, Matt LaClear sent the client an email advising him to hire a developer to clean up the infection that caused the site to crash.
We did not get a reply from the client regarding it.
This is the email Matt sent the client:

The client then reached out to the host for a resolution to the problem.
The host restored a backup of the site, and it went back online. Which they did not do for Danielle when she had asked for help several hours earlier.
On Tuesday, Matt LaClear sent the client an email advising him to hire a developer to clean up the infection that caused the site to crash.
We did not get a reply from the client regarding it.
This is the email Matt sent the client:

On 1/4/2023 at 2:30 PM, we received an email from the client stating that Japanese characters appeared in their meta titles and descriptions on Google.
This meant the spam pages the hackers inserted on the page were getting indexed by Google.
There was malware detected on January 4 by Sucuri at 4:37 PM:
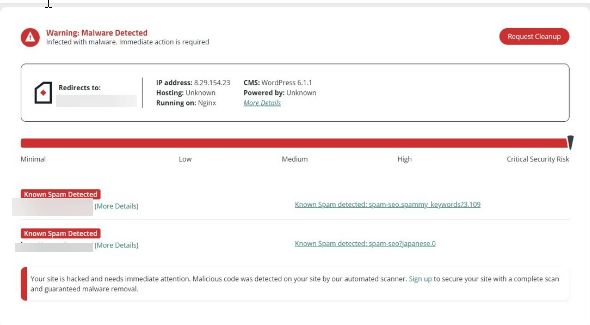
We then became very concerned that Google would deindex the entire site because of the Malware pages.
At 2:54 PM the same day, Matt informed the client that we would clean up the infection ourselves because he didn’t want them to hurt their Google rankings.
At 7:47 PM, we finished cleaning the Malware off the APP and SERVER levels of CosmoIns.com.
We then ran another Sucuri report, and the tool reported the site free of malware.

To prevent reinfection, we had our developer harden the server from the app side.
To ensure the site has not been reinfected, the developer runs scans 2x/a day to look for malware.
We also run multiple audits to find any internal links that are spammy. Nothing has been detected since the site was cleaned on 1/4/23.
Our developer then performed a Pen Test scan.
This scan tests the effectiveness of perimeter security controls to prevent and detect attacks and identify weaknesses in internet-facing assets such as web, mail, and FTP servers. He found nothing critical from the outside.
When the developer logged in the first time, Wordfence had been deactivated; he reactivated it to run internal malware scans.
We believe that the hacker deactivated it.
The developer suspected this IP was the intruder (from January 1st):

We suspected that the first payloads came directly through the WP admin panel through the admin user.
Right after that, we changed the “admin” password on WordPress.
These steps stopped further reinfection.
The hacker possibly got in through your server and hacked the GDPR plugin. There have been known vulnerabilities with that plugin recently. As well as many others.
More on that here:
The site could have been hacked Friday night, December 30th, and then reinfected the backup that the hosting installed because the hacker still had access to the server.
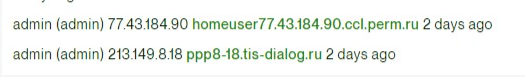
The developer found an admin login from Russia from January 2:

What follows is the type of content the hacker added to the client’s website.
We found Phishing on the website (sales forms from hackers):

We also found spam links inside the content on blog posts and pages.


Once we felt confident the site was secure, we began our efforts to clean up the Google index for the client’s domain.
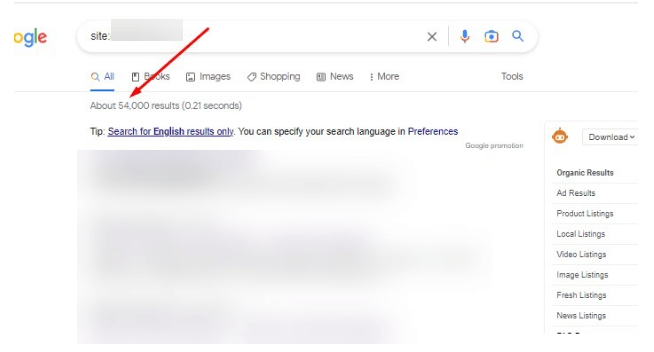
The site has 2500 or so indexed pages when clean of malware.
The screenshot below shows the high water mark of the damage where over 51,000 malware pages were indexed on their domain:
To remedy the problem, we scraped the index to find the malware pages we needed to remove using Google Removal Tool.
The first tool we used to scrape the indexed pages on the domain was Google Search Console (GSC). Using it, we found 1000 pages fast that we needed to get Google to delete from the index.
We then added those URLs to the Google Removal Tool, and Google deindexed them a couple of hours later.
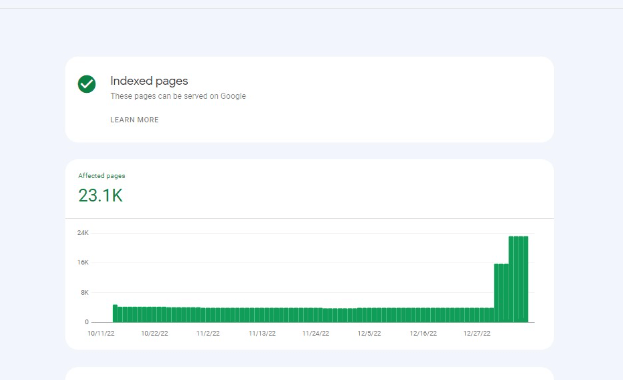
Here is the screenshot from inside GSC showing over 23,000 indexed pages for a site that generally has 3700 indexed pages:
Unfortunately, the Google Removal Tool only allows for a maximum of 1000 URLs a day.
When we hit our quota for the day, we received the message below, captured in the screenshot:

The tool’s 1000 URL a day maximum forced us to spread our clean-up efforts over several days, given we had close to 50,000 pages to delete.
It was the number one bottleneck to getting the index cleaned much faster.
Here is a screenshot of our team using the Google Removal Tool:

On 1/5/2023, the Japanese characters were cleaned up when searching for client brand name on Google.
On 1/17/2023 client’s Google listings were now clear of the spammed pages and our work completed on the project.

At Your SEO Squad, we make sure that your website stays safe from any bad people who might want to cause trouble. Our team is super fast and reliable, so if something bad happens, we’ll be there right away with help so that very little of your business is affected.
We go step by step to ensure everything that was done by the bad guys has been taken care of, like making sure every mention of your site online is true and security is strong. Then, you can rest easy knowing that your data is secured and your online presence is back in good shape.
Call us at (517) 512-9543 to get the ball rolling!
Copyright Digital Wins 2024